How to configure AzureAD
This guide demonstrates how to configure Single Sign-On (SSO) integration between Port and Microsoft Entra ID (AzureAD) using OIDC.
Once implemented:
- Users can connect to Port via an AzureAD app.
- AzureAD teams will be automatically synced with Port upon user sign-in.
- You can set granular permissions in Port according to your AzureAD groups.
Prerequisites
Before starting the configuration, ensure you have:
- Access to the Microsoft Azure Portal with permissions to create and configure applications.
- Users who need access to Port must have a valid value in their
Emailfield in Azure AD. - Contact information ready to share with Port support team for the final configuration steps.
To complete the process you will need to contact us to receive the information you require, as well as provide Port with specific application details outlined in this guide.
Register a new application
Create the application registration
-
In the Microsoft Azure Portal, go to
Azure Active Directory. -
Click on
App registrations.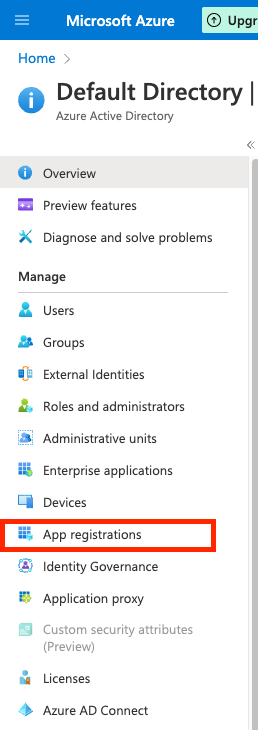
-
Click on
New registrationat the top of the page.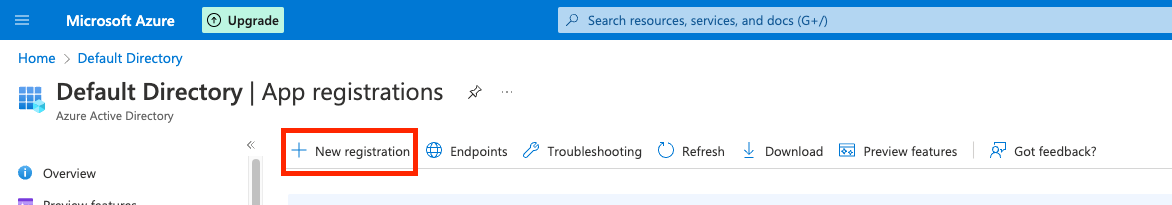
-
Define the Port application settings:
4.1 Name: Insert a friendly name for the Port app, like
Port.4.2 Supported account types: Please select the option that is appropriate for your organization.
For most use cases this would be Accounts in this organizational directory only (Default Directory only - Single tenant).
4.3 Redirect URI:
-
Set
PlatformtoWeb -
Set
URLtohttps://auth.getport.io/login/callback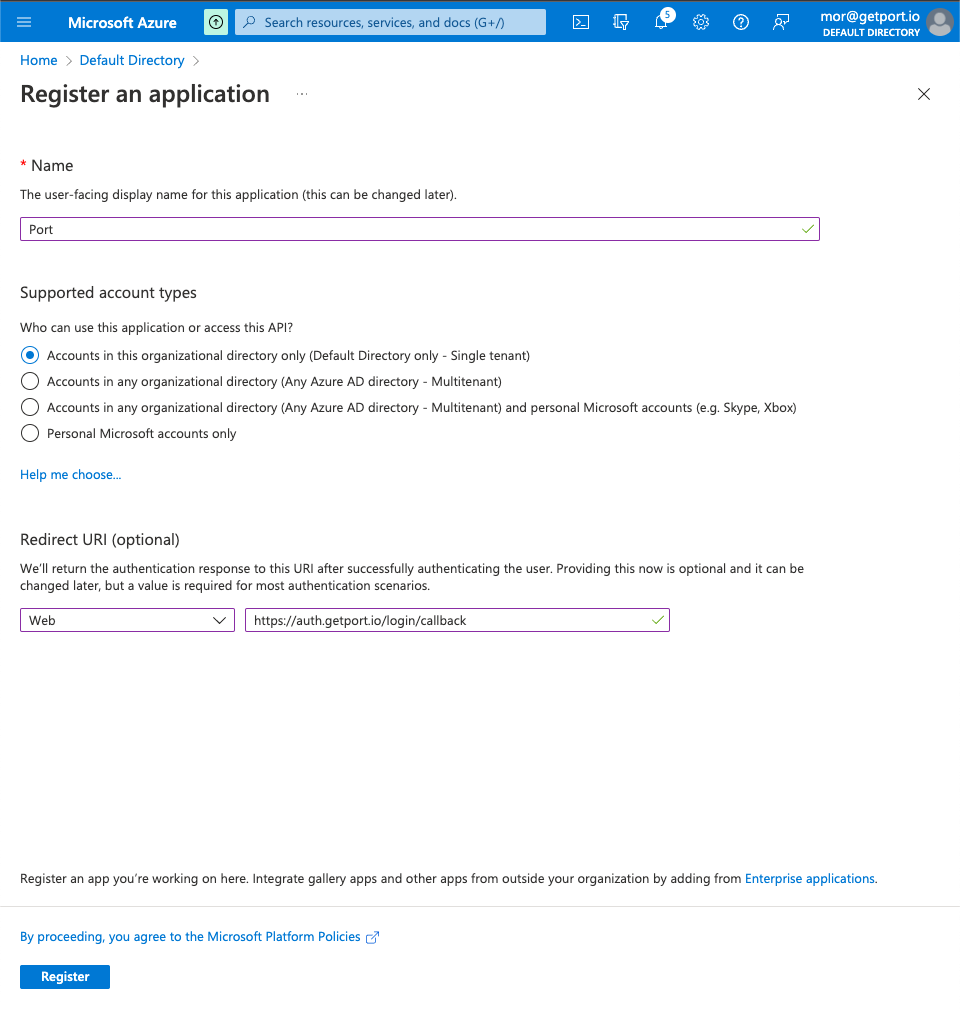
4.4 Click
Register. -
Configure authentication settings
-
On the new Port App page, click
Authentication.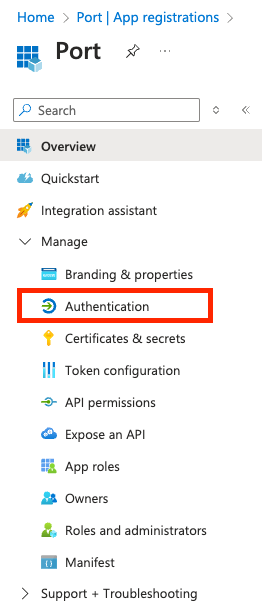
-
Add the Front-channel logout URL: paste the following URL:
https://auth.getport.io/logoutAdding the front-channel logout URL will enable single sign-out, meaning when a user logs out from Port, it also logs them out from their identity provider.
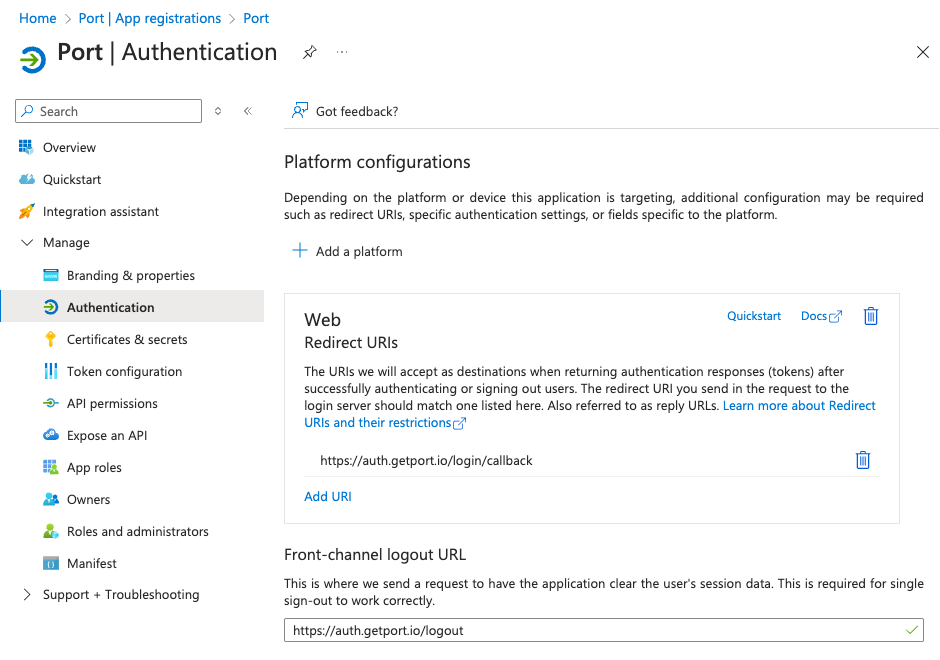
-
Click
Save.
Configure application branding
-
On the new Port App page, click
Branding & Properties.
-
Configure the following settings:
2.1 Home page URL: paste the following URL:
Setting authorization endpoint based on account regionPort exposes two API instances, one for the EU region of Port, and one for the US region of Port.
Use the correct endpoint based on your account region, and make sure to to replace{CONNECTION_NAME}with the value provided to you by Port.- EU
- US
https://auth.getport.io/authorize?response_type=token&client_id=96IeqL36Q0UIBxIfV1oqOkDWU6UslfDj&connection={CONNECTION_NAME}&redirect_uri=https%3A%2F%2Fapp.getport.iohttps://auth.us.getport.io/authorize?response_type=token&client_id=4lHUry3Gkds317lQ3JcgABh0JPbT3rWx&connection={CONNECTION_NAME}&redirect_uri=https%3A%2F%2Fapp.us.getport.ioWe will provide your
{CONNECTION_NAME}(Contact us using chat/Slack/mail to support@getport.io).2.2 Publisher domain: Select the domain matching your user emails (for example
getport.io).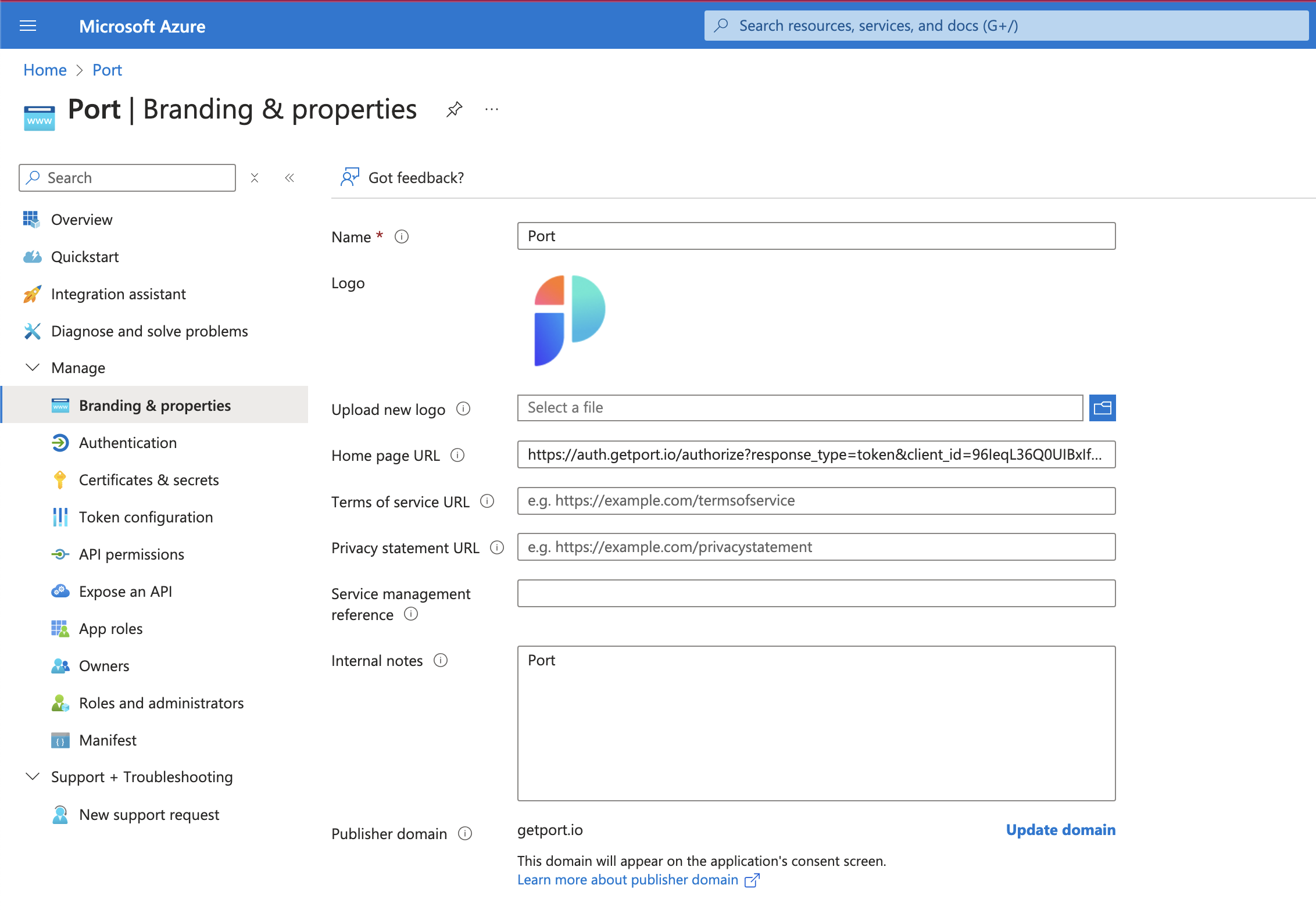
-
Click
Save.
Set up application permissions
Add required permissions
-
On the Port App page, click
API Permissions.
-
Click
Add a permission.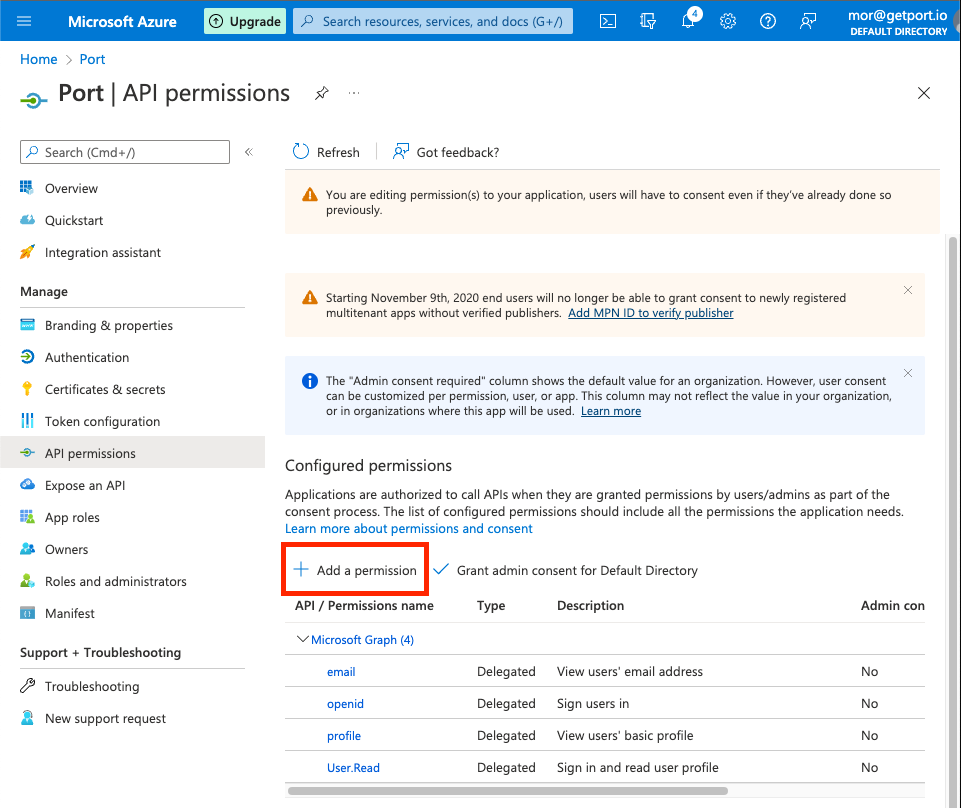
-
On the
Microsoft APIstab:3.1 Click on
Microsoft Graph.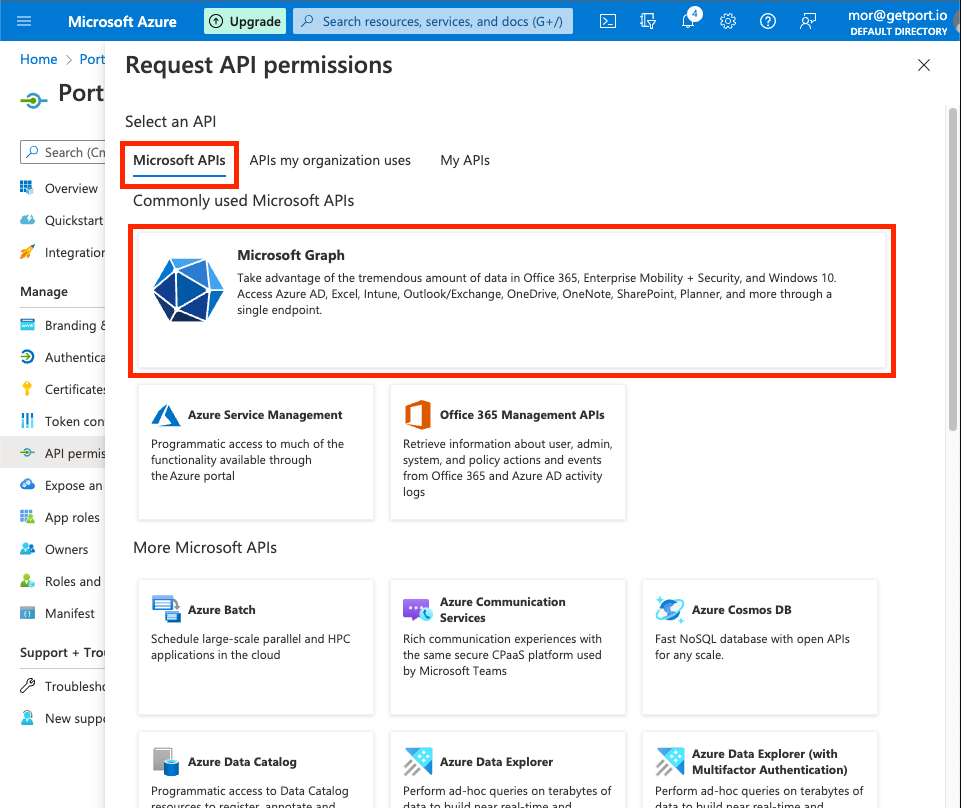
3.2 Click on
Delegate Permissions.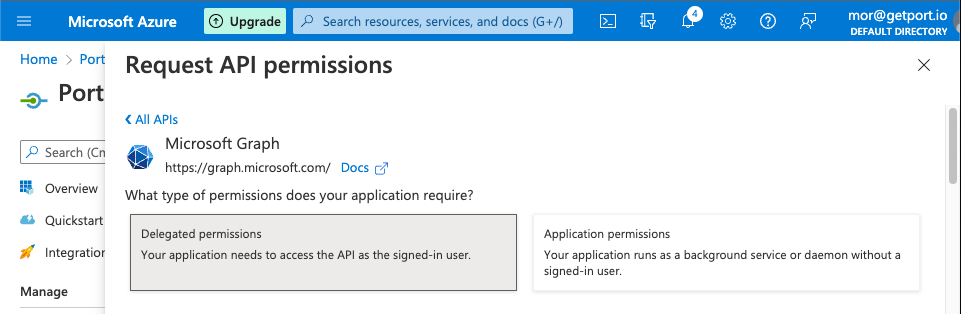
3.3 Search and mark the following permissions:
email,openid,profile,User.read
AzureAD groups integrationIf you wish to pull in AzureAD groups into Port, you will also need to add the
Directory.Read.Allpermission.
See Permissions required to pull AzureAD groups to Port for more details.
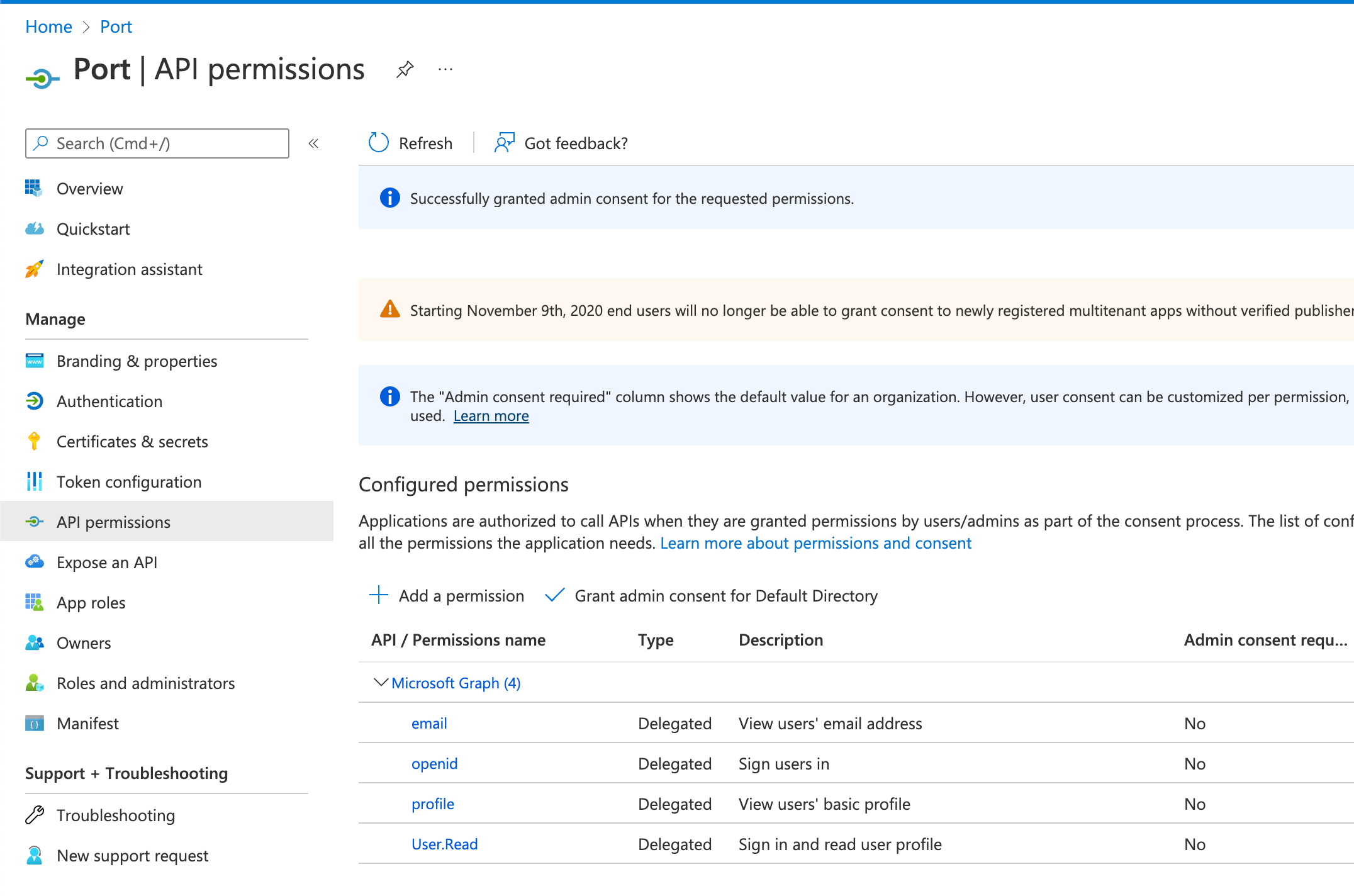
3.4 Click
Add permissions.Grant admin consent(OPTIONAL)
Grant admin consent: when users from your organization will first log in, they will be prompted to confirm the permissions specified here. You can click theGrant admin consent for Default Directoryto automatically approve their permissions.
Configure application claims
Add optional claims
-
On the Port App page, click
Token configuration.
-
Click
Add optional claim.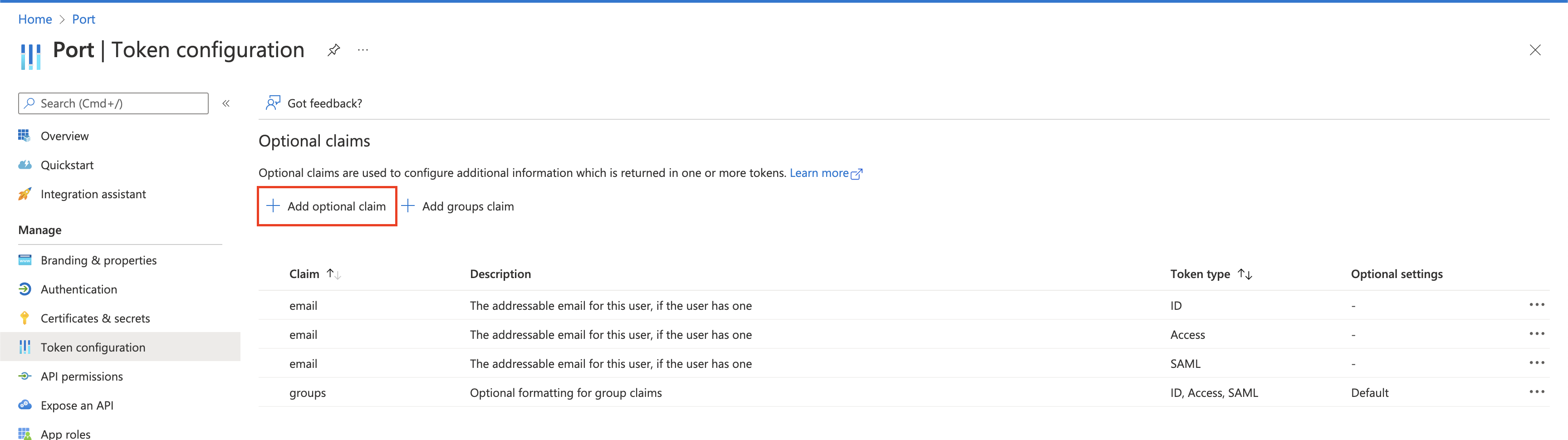
-
Select
IDas the token type and then select theemailclaim, then clickAdd.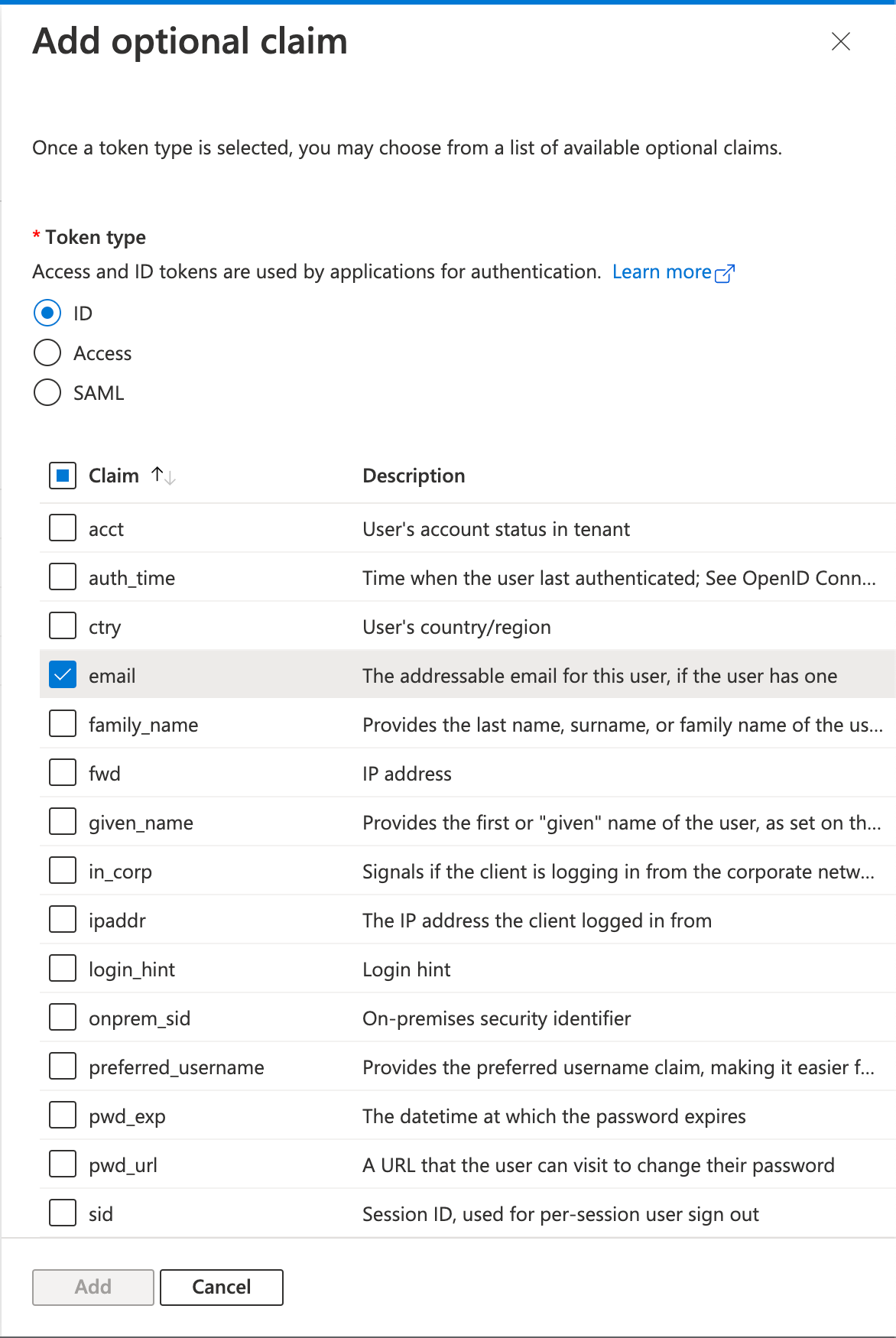
Repeat the same process for
AccessandSAML(3 times total). -
Your optional claims will look like this:
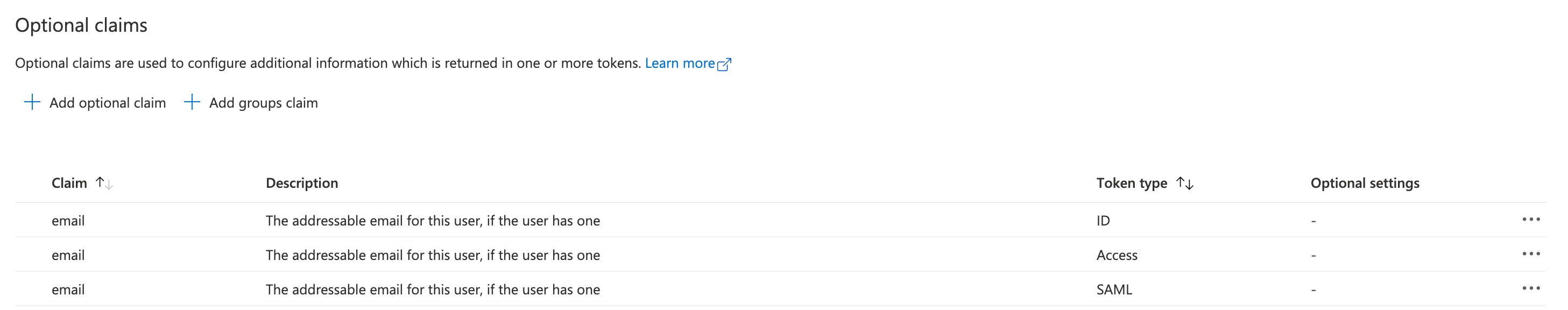
Generate application secret
Create client secret
-
On the Port App page, click
Certificates & Secrets.
-
On the
Client secretstab, click theNew client secretbutton.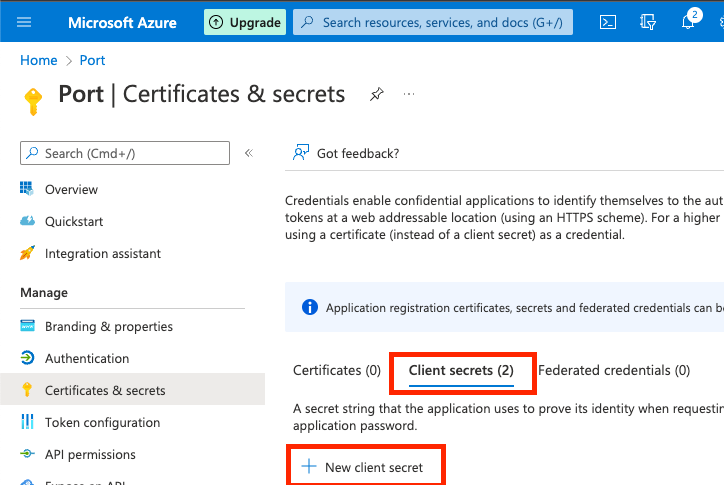
-
Configure the secret:
3.1 Description: Enter a secret description, for example
Port Login Client Secret.3.2 Expires: Select when the secret expires.
Be sure to mark on your calendar the expiration date of the secret. The secret needs to be replaced before its expiration, otherwise login to Port will be disabled.
3.3 Click
Add. -
Copy the secret immediately: A secret will be created and its Value will appear as shown in the image below. Document the secret's value immediately because it will never appear again after you leave this page.
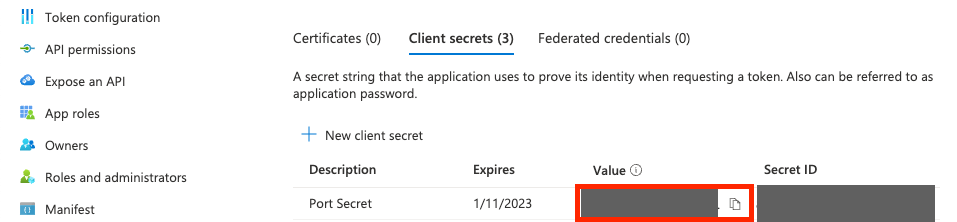
Provide application information to Port
Port needs the following information to complete the integration:
- The
Client Secretvalue that you created in the previous step. - The
Application (Client) ID, which appears on the Port application overview page:
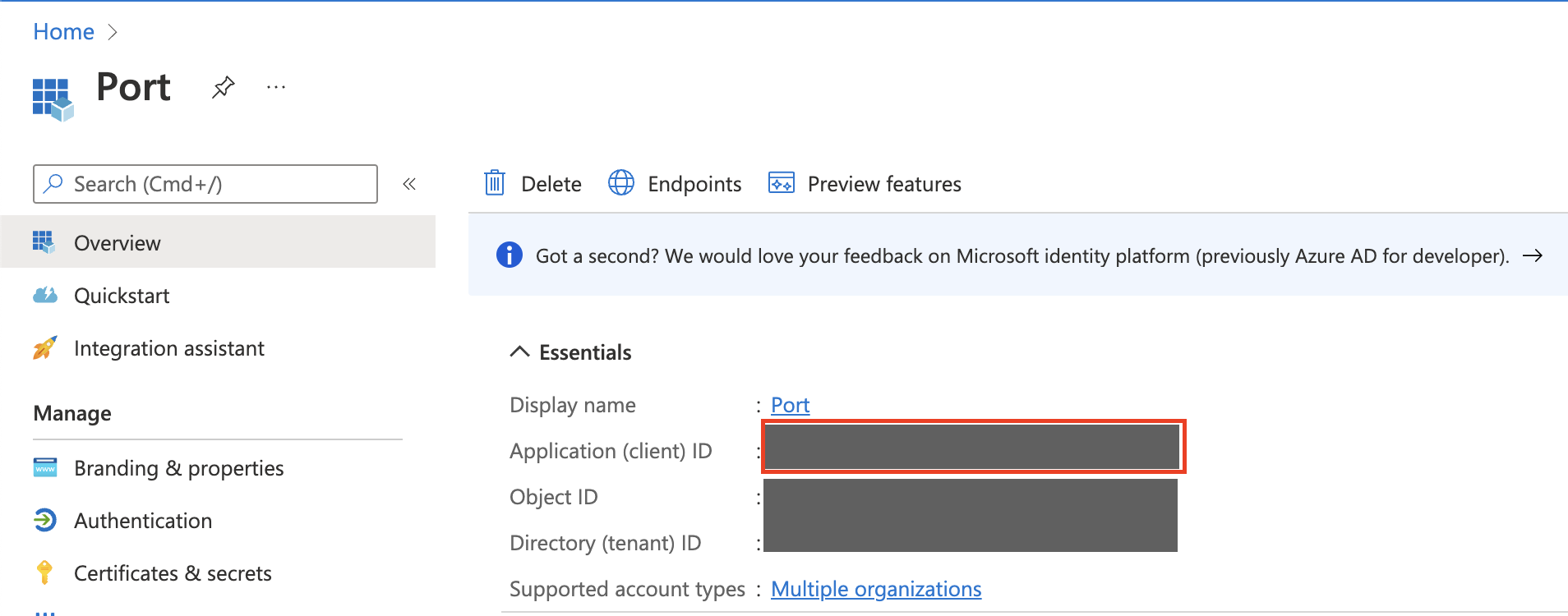
Port will provide you the CONNECTION_NAME needed for the homepage URL of the App.
Distribute the application to users
Assign users and groups
After the app setup is complete, you can assign it to your organization's users and groups:
-
Go to
Azure Active Directory. -
Go to
Enterprise Applications.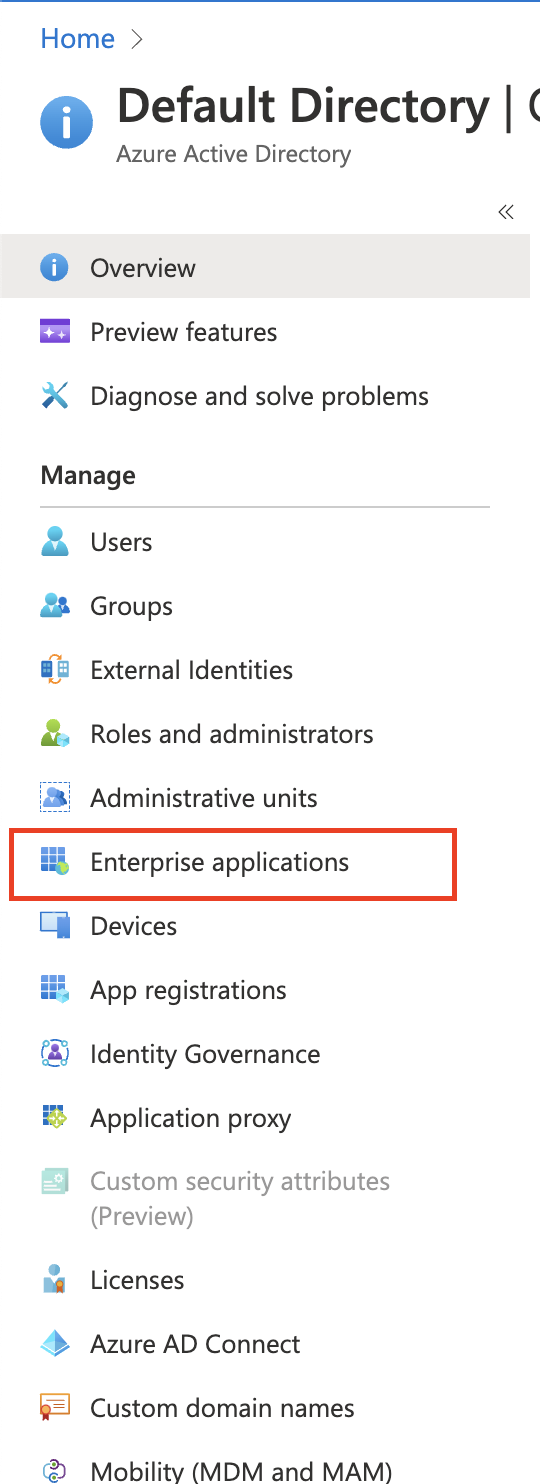
-
Click on the Port app.
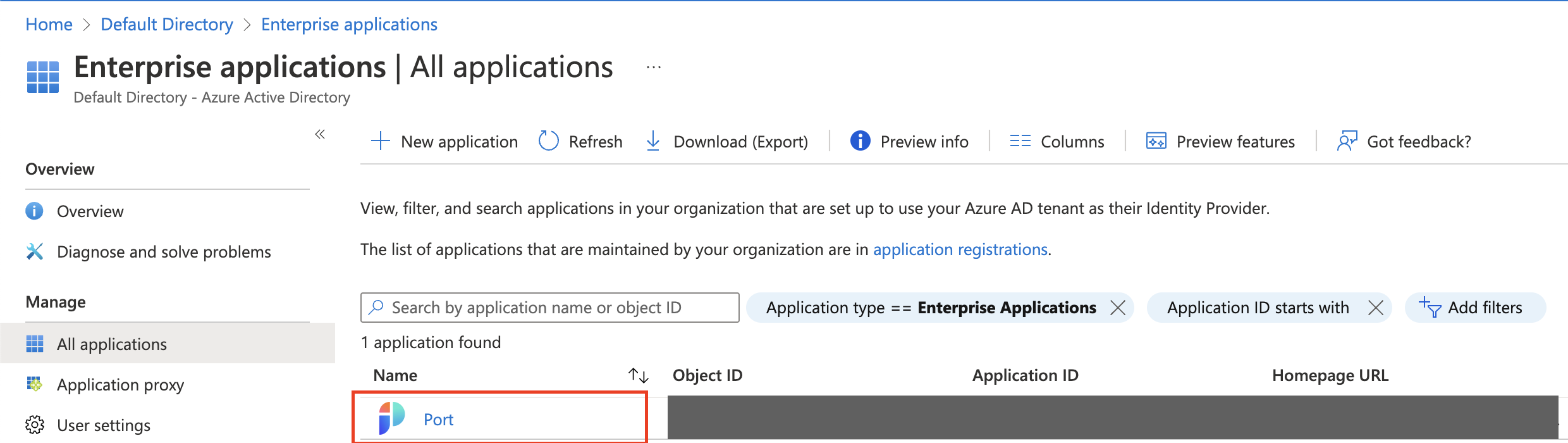
-
Click on
Users and Groups.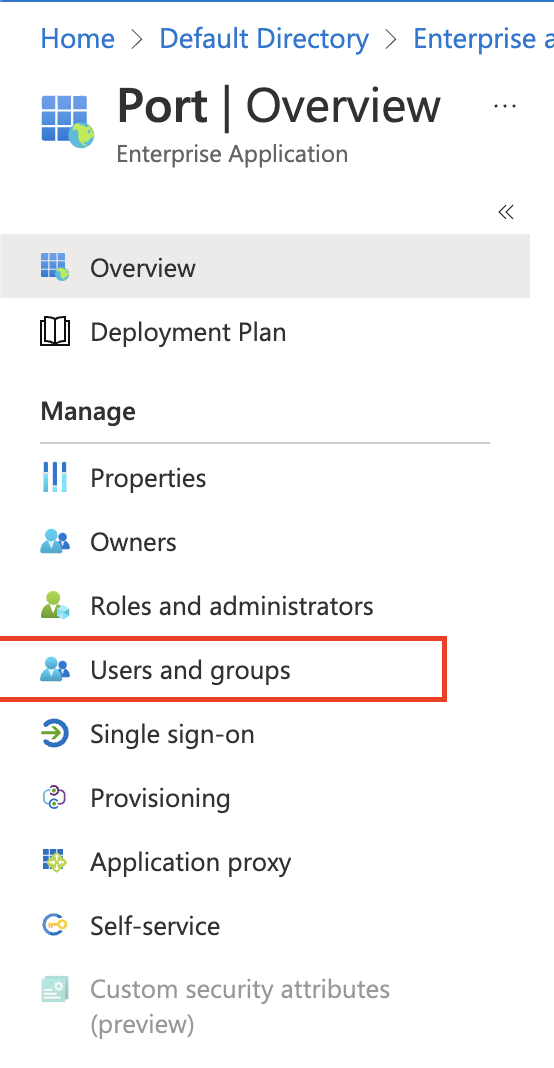
-
Click
Add user/group.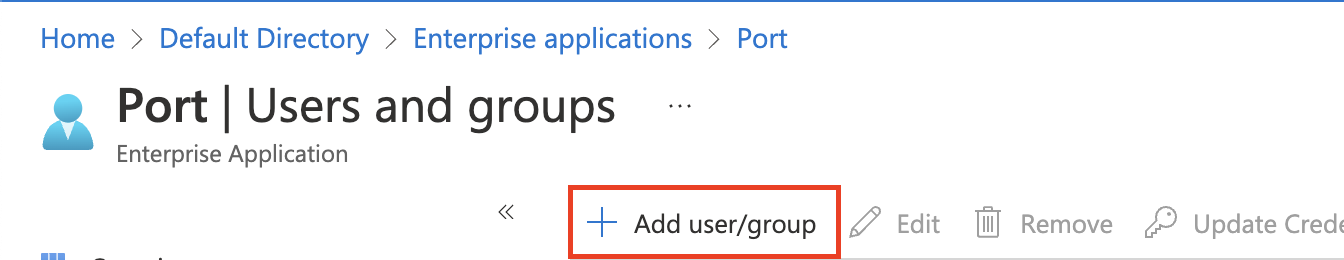
-
Select users and groups you want to grant access to Port, then click
Assign.
Make the application visible
-
Go to
Azure Active Directory>Enterprise Applications> Port app. -
Click on
Properties.
-
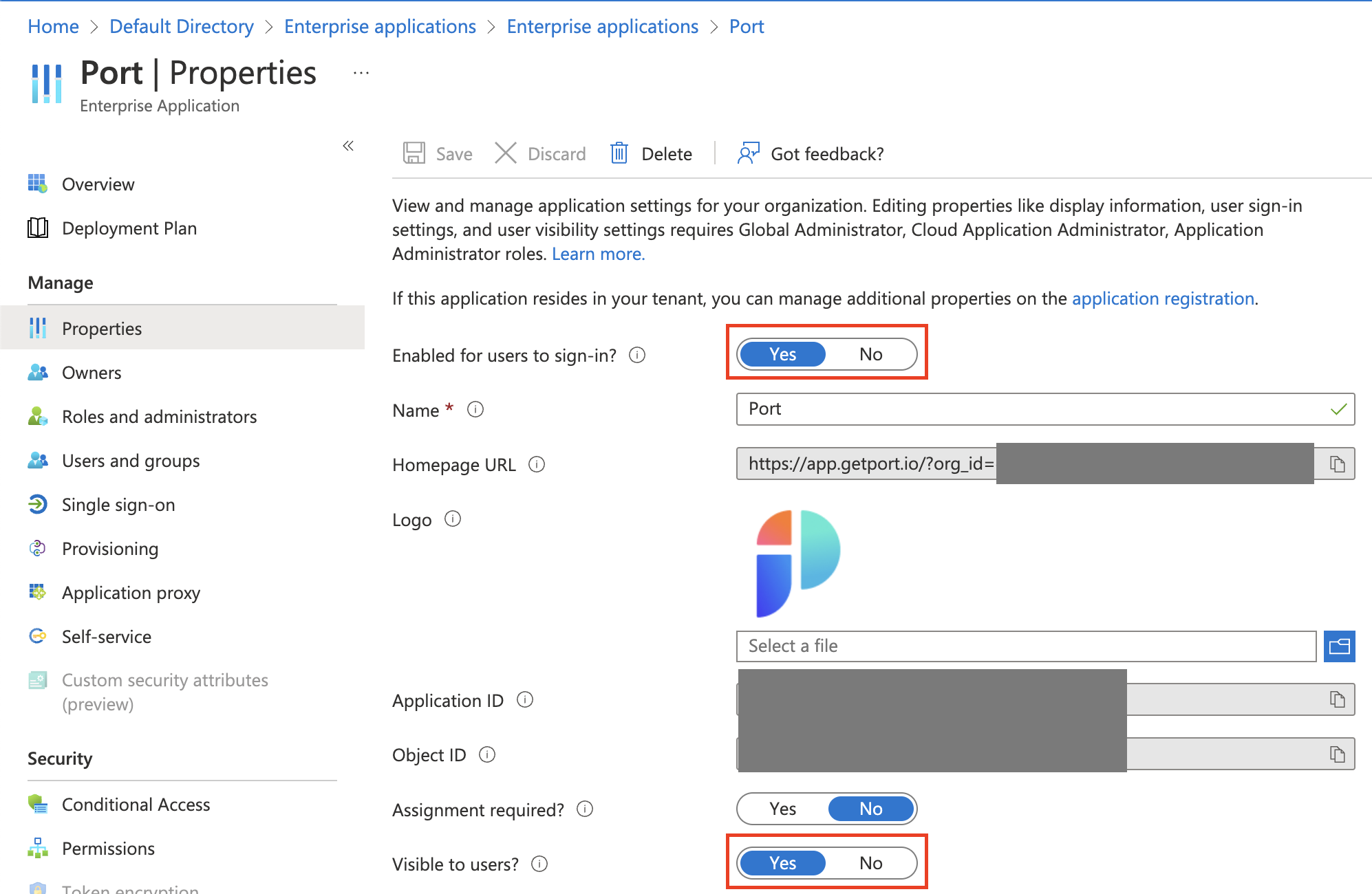
Set the application properties:
- Mark
Enabled for users to sign-in?asYes. - Mark
Visible to users?asYes.
Assignment required?By default the
Assignment required?flag is set toNo, meaning any user with the Homepage URL to the Port app can access it, even if the app isn't directly assigned to them. Changing the flag toYesmeans only users and groups the app is directly assigned to can use and access it.
- Mark
-
You should see the Port app on the https://myapplications.microsoft.com dashboard:
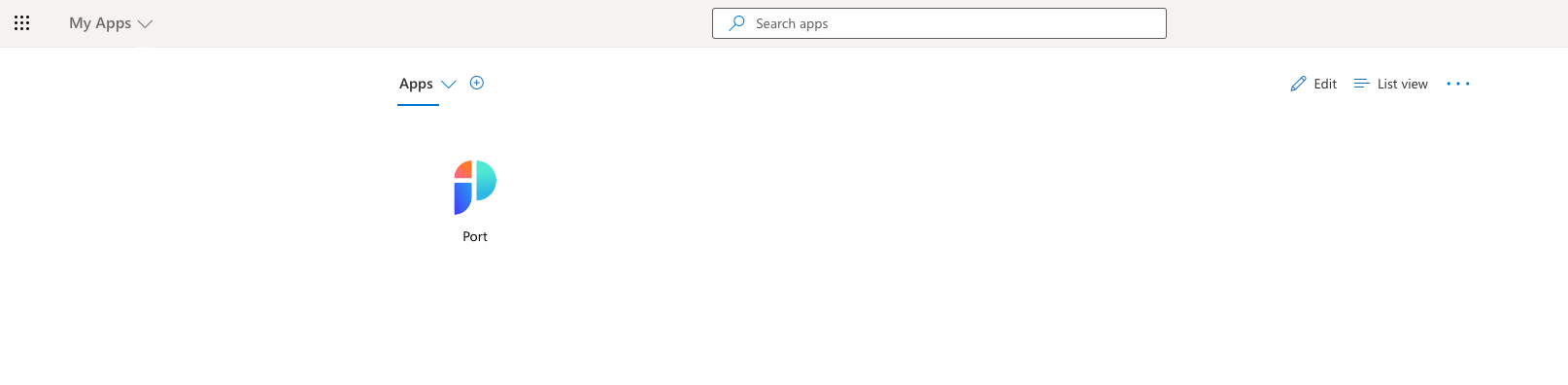
Users can also manually access Port by going to the App Homepage URL.
Multiple Azure AD SSO connections
If you have multiple Port environments, it is possible to setup an OIDC Azure AD SSO connection for each environment.
However, note that in this instance you will not be able to use Port's main login page to reliably sign in to a specific environment. When you enter your email address to login, it will take you to one of your Port environments but it is not guaranteed to take you to the same Port environment every time.
In that case you have the following options:
- Use the https://myapplications.microsoft.com dashboard provided by Azure AD and select the desired Port environment to connect to.
- Use the manual login URL for each environment directly, by specifying the desired environment based on its respective
CONNECTION_NAMEvalue.
Enable AzureAD groups integration
Port can query the group membership of users who log in through the AzureAD SSO, and add their teams as team entities inside Port. This allows platform engineers to take advantage of both existing groups from AzureAD and teams created manually inside Port to manage permissions and access to resources inside Port's catalog.
In order to import Azure AD groups into Port, Port will require the connection app to approve the Directory.Read.All permission.
SCIM Configuration (beta)
Due to technical limitations, OIDC integrations do not directly support SCIM. You will be required to set up another application, which will be handle provisioning based on the SCIM protocol.
With SCIM in place, in order to grant the user access to Port, you will need to assign the user both the primary SSO application and to the SCIM application.
Entra ID (AzureAD) OIDC applications support SCIM.
Functionality enabled by SCIM
By enabling SCIM the following functionality will be enabled:
- Automatic deprovisioning of users (for example, when a user is unassigned from the SSO application, that user will automatically lose access to Port).
Limitations
- Does not support user provisioning - Only deprovisioning is supported; users must be created manually or through SSO login.
- Does not sync user attribute updates - Changes to user profiles in your identity provider will not automatically update in Port.
- Does not support group provisioning - Group membership changes in your identity provider are not synchronized via SCIM.
- Does not provide real-time sync - SCIM operations may have delays and are not instantaneous.
- Does not support custom user attributes - Only standard user fields are processed during deprovisioning.
- Only supported for customers with a single workspace - SCIM is not available for multi-workspace setups.
For full user and group synchronization, rely on the SSO login process rather than SCIM.
Set up SCIM
To set up SCIM for Entra ID OIDC based applications, contact Port's support team.
You will be provided with:
- An SCIM
endpoint. - An SCIM
token.
The endpoint and token will be used to set up the SCIM integration in your identity provider.
After receiving the SCIM endpoint and token, follow this step-by-step guide to enable SCIM. Begin in step 3, by registering a new application.